라우팅 설정 및 AH-ESP 터널모드 구성

[ 01. 라우터 설정 ]
- Tera Term 프로그램 > 메뉴 > 새로만들기
- 호스트 : 127.0.0.1 (localhost)
- 서비스 : Telnet
- TCP 포트 : 5000-5003 (R1-R4)
============================================================
[ 02. 라우팅 테이블 등록 및 활성화 작업 (초기 세팅) ]
# config 모드 진입
configure terminal
# loopback 0번 인터페이스로 진입해서 해당 ip 등록
# R1: 172.16.1.1 / R2 : 172.16.2.1 / ...
interface loopback 0
ip address 172.16.1.1 255.255.255.0
# 라우터 활성화 상태 유지 및 config 모드 종료
no shutdown
end
# 라우팅 설정 확인
# 172.16.1.0 대역으로 들어오면 loopback 0 으로 보내겠다
show ip route
>> 172.16.1.0 is directly connected, Loopback0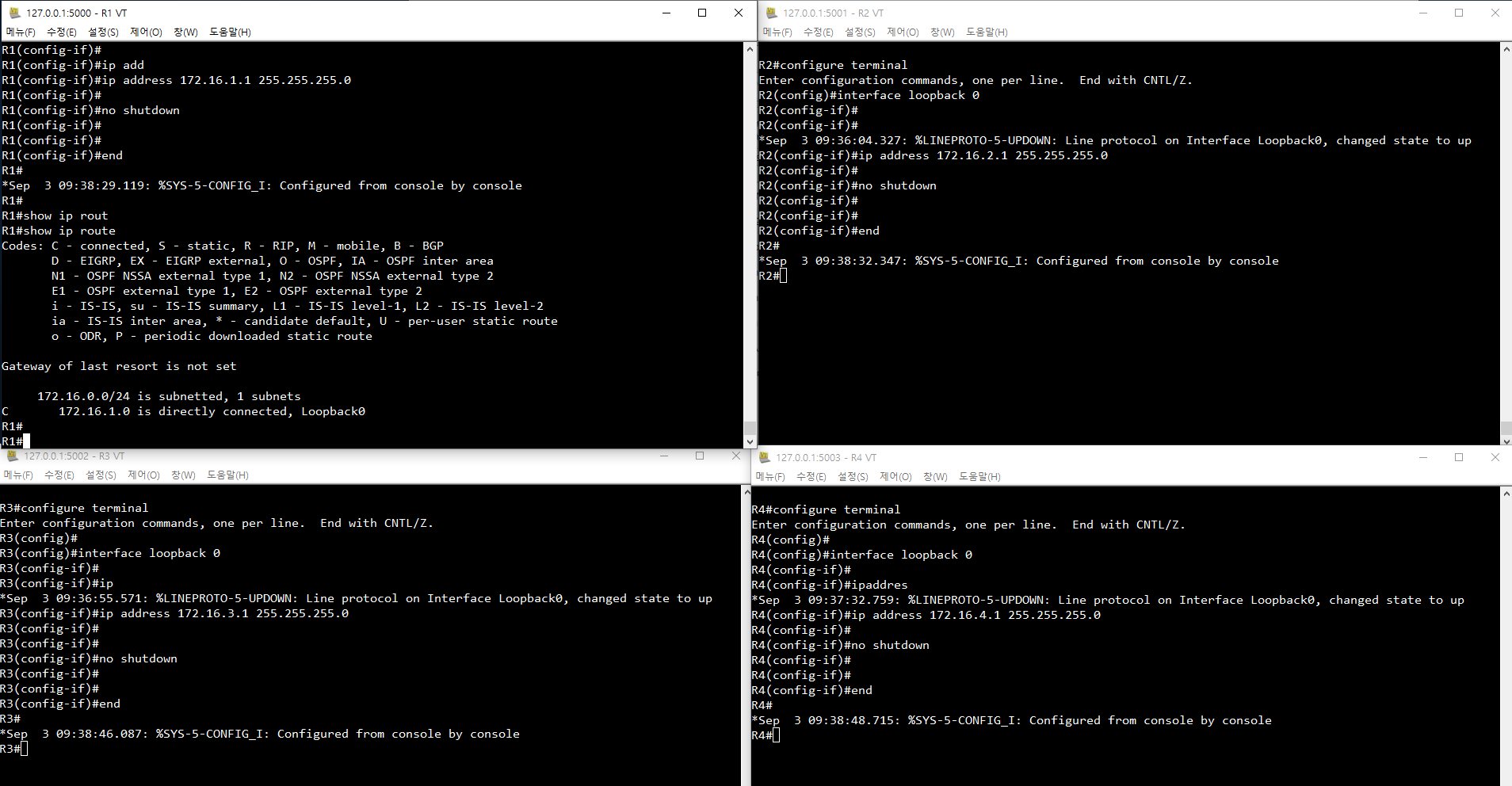
============================================================
[ 03. 라우터 구성 작업 ]
=================== <R1> ===================
configure terminal
interface serial 1/1
ip address 192.168.12.1 255.255.255.0
no shutdown
=================== <R2> ===================
configure terminal
interface serial 1/2
ip address 192.168.12.2 255.255.255.0
no shutdown
exit
interface serial 1/1
ip address 192.168.23.1 255.255.255.0
no shutdown
=================== <R3> ===================
configure terminal
interface serial 1/2
ip address 192.168.23.2 255.255.255.0
no shutdown
exit
interface serial 1/1
ip address 192.168.34.1 255.255.255.0
no shutdown
=================== <R4> ===================
configure terminal
interface serial 1/2
ip address 192.168.34.2 255.255.255.0
no shutdown
============================================================
[ 04. 라우팅테이블 확인 ]
**R1,4
# end
# show ip route --> R1,4 : 맨 끝 라우터니까 C(connected) 가 2줄 뜸


**R2,3
# end
# show ip route --> R2,3 : 중간에 있는 라우터니까 C 가 3줄 뜸


============================================================
[ 05. 라우팅 패킷 덤프 (캡처) ]

============================================================
[ 06. 라우팅테이블 정보 전달 ]
*rip(routing information protocol) : 내가 알고있는 정보를 상대방에게 넘기겠다
- 각 라우터가 알고있는 정보 : C가 뜨던 줄
- C : connect
- R : RIP (Routing Information Protocol)
R1# configure terminal
R1(config)# router rip
R1(config-router)# version 2
R1(config-router)# no auto-summary
# 각 라우터 별 정보 전달
R1(config-router)# network 172.16.1.0
R1(config-router)# network 192.168.12.0
R1(config-router)# end
R2(config-router)# network 172.16.2.0
R2(config-router)# network 192.168.12.0
R2(config-router)# network 192.168.23.0
R2(config-router)# end
R3(config-router)# network 172.16.3.0
R3(config-router)# network 192.168.23.0
R3(config-router)# network 192.168.34.0
R3(config-router)# end
R4(config-router)# network 172.16.4.0
R4(config-router)# network 192.168.34.0
R4(config-router)# end

show ip route rip- R1 : R2 한테 자신의 정보를 전달
- R2 : R1, R3 한테 자신의 정보를 전달
- R3 : R2, R4 한테 자신의 정보를 전달
- R4 : R3 한테 자신의 정보를 전달
show ip interface brief- 물리층, 데이터 링크층의 'up', 'down' 상태 및 IP 주소 정보 확인
wr- 지금까지의 설정 저장
============================================================
[ 07. R1 - R4 IPSec VPN 설정 4가지 ]
- R2, R3는 설정할 필요 없음 (R1, R4만 필요)
1) AH - 축약 모드
=================== <R1> ===================
# config 모드 진입
configure terminal
crypto isakmp policy 10
encryption des
group 2
hash md5
authentication pre-share
lifetime 60
exit
crypto isakmp peer address 192.168.34.2
set aggressive-mode password 1234
set aggressive-mode client-endpoint ipv4-address 172.16.4.1
ip access-list extended R1R4
permit ip 172.16.1.0 0.0.0.255 172.16.4.0 0.0.0.255
exit
crypto ipsec transform-set KITRI ah-md5-hmac
exit
crypto map VPN 10 ipsec-isakmp
match address R1R4
set peer 192.168.34.2
set transform-set KITRI
exit
interface serial 1/1
crypto map VPN
end
=================== <R4> ===================
# config 모드 진입
configure terminal
crypto isakmp policy 10
encryption des
group 2
hash md5
authentication pre-share
lifetime 60
exit
crypto isakmp peer address 192.168.12.1
set aggressive-mode password 1234
set aggressive-mode client-endpoint ipv4-address 172.16.1.1
ip access-list extended R4R1
permit ip 172.16.4.0 0.0.0.255 172.16.1.0 0.0.0.255
exit
crypto ipsec transform-set KITRI ah-md5-hmac
exit
crypto map VPN 10 ipsec-isakmp
match address R4R1
set peer 192.168.12.1
set transform-set KITRI
exit
interface serial 1/2
crypto map VPN
end
=================== <추가 확인> ===================
[동작 확인]
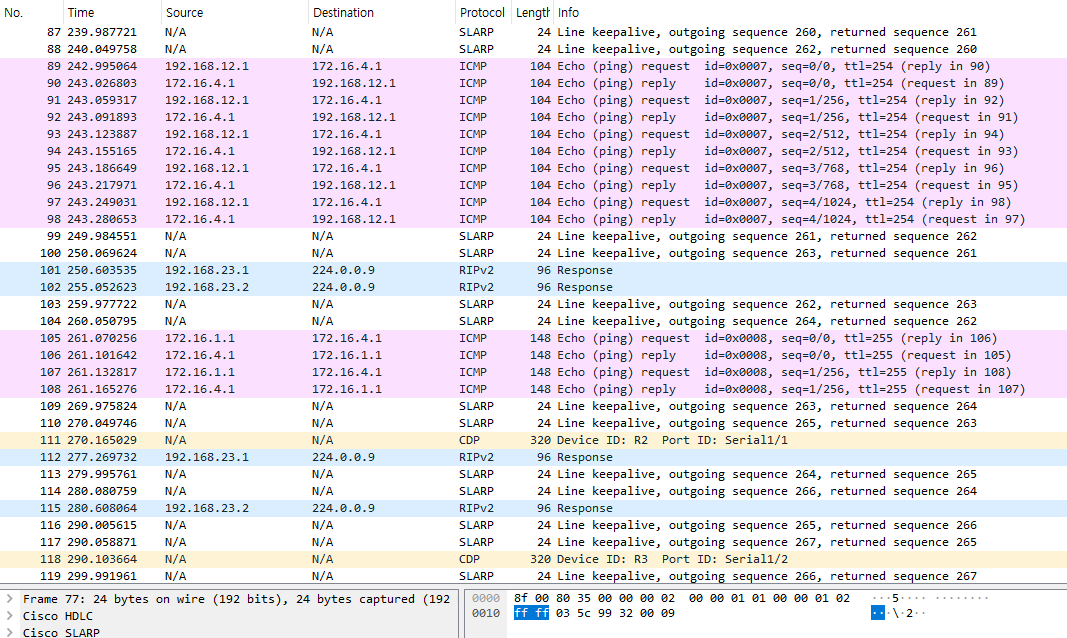
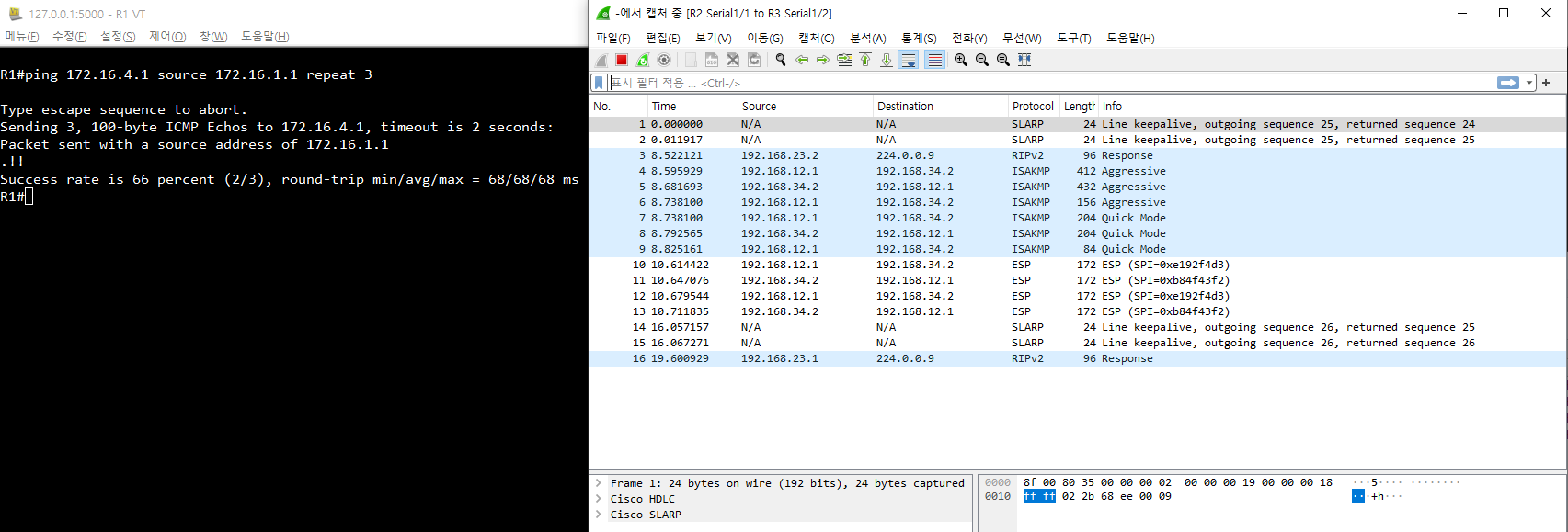
ping 172.16.1.1 source 172.16.4.1 repeat 3
[피어 상태 확인]
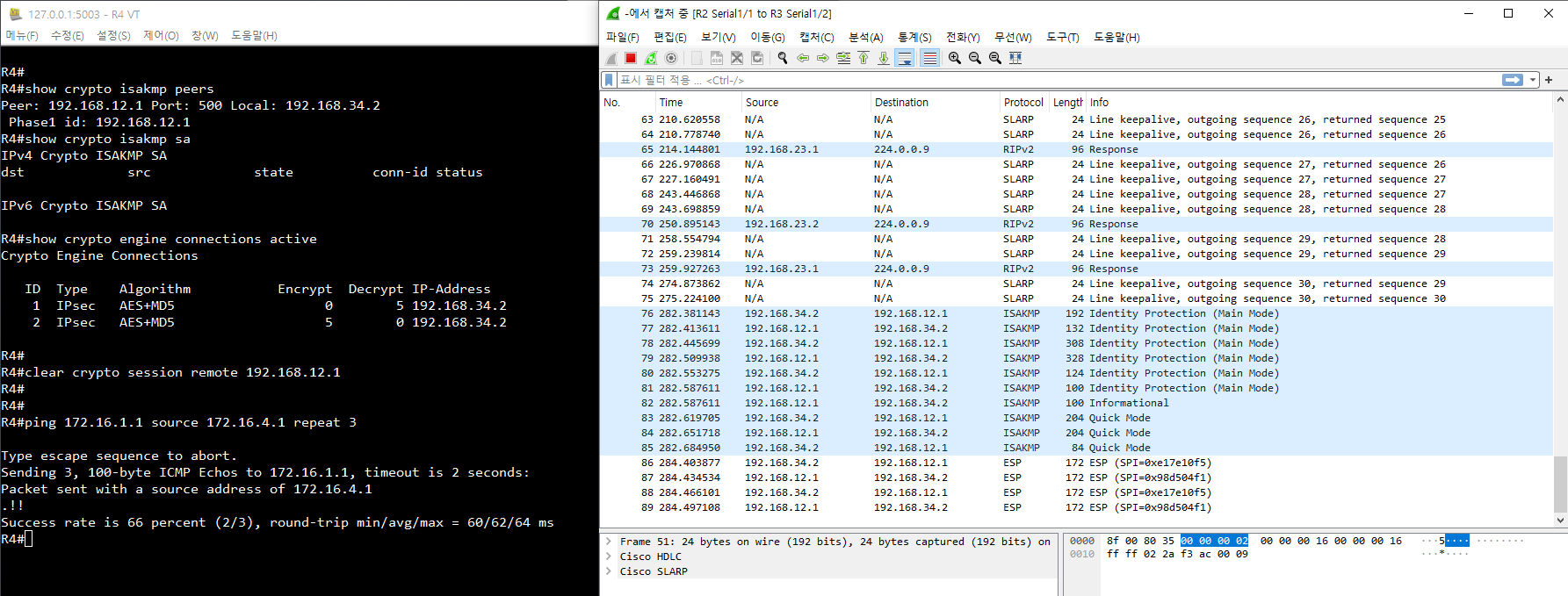
show crypto isakmp peers
[SA 상태 확인]
show crypto isakmp sa
[연결 상태 확인]
show crypto engine connections active [연결 재시작]
clear crypto session remote 192.168.12.1
- ping(패킷) 나가는게 적나라하게 보임
2) AH - Main 모드

=================== <R1> ===================
# config 모드 진입
crypto isakmp policy 10
encryption des
group 2
hash md5
authentication pre-share
lifetime 60
exit
crypto isakmp key 1234 address 192.168.34.2
ip access-list extended R1R4
permit ip 172.16.1.0 0.0.0.255 172.16.4.0 0.0.0.255
exit
crypto ipsec transform-set KITRI ah-md5-hmac
exit
crypto map VPN 10 ipsec-isakmp
match address R1R4
set peer 192.168.34.2
set transform-set KITRI
exit
interface serial 1/1
crypto map VPN
end
=================== <R4> ===================
# config 모드 진입
crypto isakmp policy 10
encryption des
group 2
hash md5
authentication pre-share
lifetime 60
exit
crypto isakmp key 1234 address 192.168.12.1
ip access-list extended R4R1
permit ip 172.16.4.0 0.0.0.255 172.16.1.0 0.0.0.255
exit
crypto ipsec transform-set KITRI ah-md5-hmac
exit
crypto map VPN 10 ipsec-isakmp
match address R4R1
set peer 192.168.12.1
set transform-set KITRI
exit
interface serial 1/2
crypto map VPN
end
=================== <추가 확인> ===================
[동작 확인]
ping 172.16.1.1 source 172.16.4.1 repeat 3
[피어 상태 확인]
show crypto isakmp peers
[SA 상태 확인]
show crypto isakmp sa
[연결 상태 확인]
show crypto engine connections active [연결 재시작]
clear crypto session remote 192.168.12.1
- ping (패킷) 나가는게 숨겨짐
- Main Mode > Quick Mode


3) ESP - 축약 모드
=================== <R1> ===================
# config 모드 진입
crypto isakmp policy 10
encryption des
group 2
hash md5
authentication pre-share
lifetime 60
exit
crypto isakmp peer address 192.168.34.2
set aggressive-mode password 1234
set aggressive-mode client-endpoint ipv4-address 172.16.4.1
ip access-list extended R1R4
permit ip 172.16.1.0 0.0.0.255 172.16.4.0 0.0.0.255
exit
crypto ipsec transform-set KITRI esp-md5-hmac esp-aes
exit
crypto map VPN 10 ipsec-isakmp
match address R1R4
set peer 192.168.34.2
set transform-set KITRI
exit
interface serial 1/1
crypto map VPN
end
=================== <R4> ===================
# config 모드 진입
crypto isakmp policy 10
encryption des
group 2
hash md5
authentication pre-share
lifetime 60
exit
crypto isakmp peer address 192.168.12.1
set aggressive-mode password 1234
set aggressive-mode client-endpoint ipv4-address 172.16.1.1
ip access-list extended R4R1
permit ip 172.16.4.0 0.0.0.255 172.16.1.0 0.0.0.255
exit
crypto ipsec transform-set KITRI esp-md5-hmac esp-aes
exit
crypto map VPN 10 ipsec-isakmp
match address R4R1
set peer 192.168.12.1
set transform-set KITRI
exit
interface serial 1/2
crypto map VPN
end
=================== <추가 확인> ===================
[동작 확인]
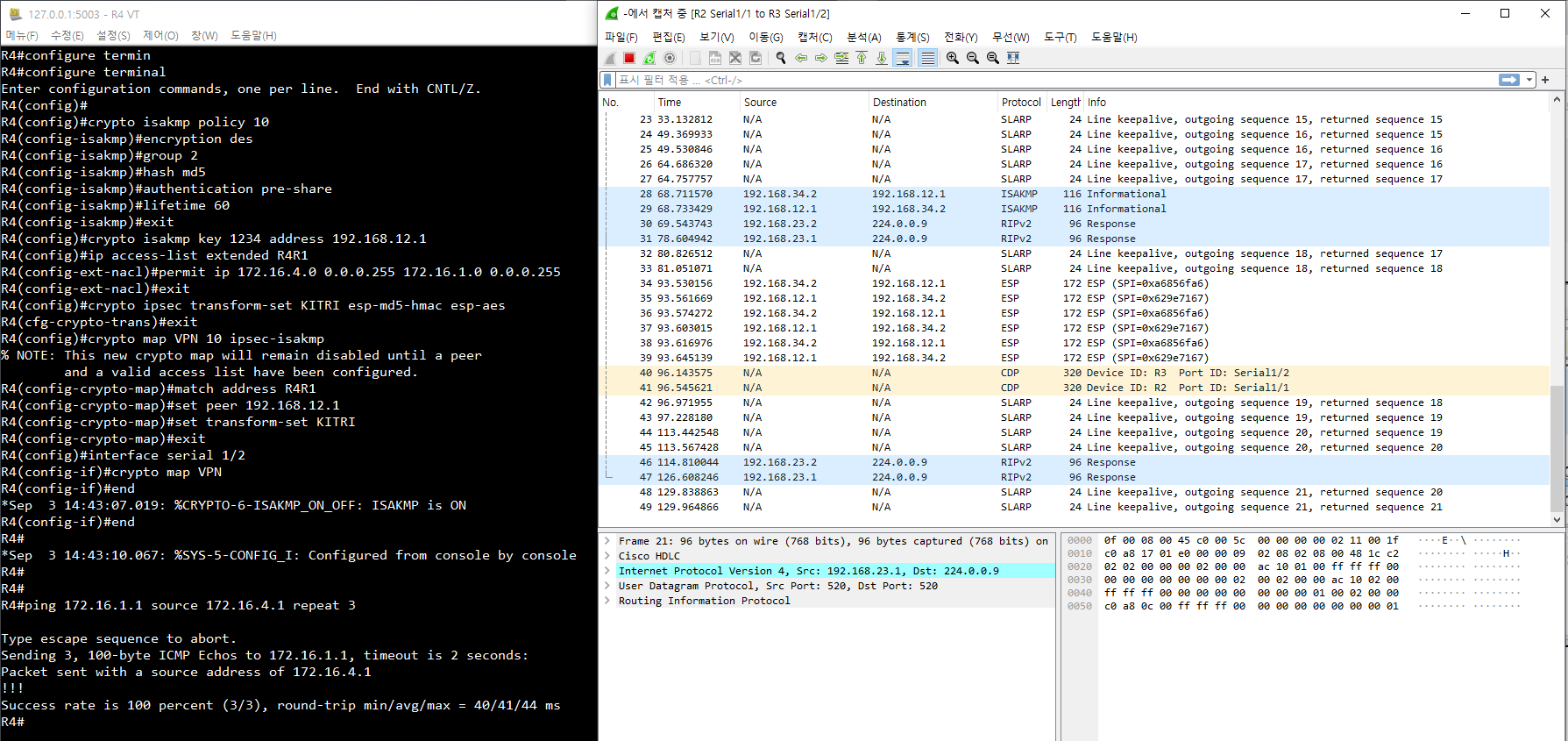
ping 172.16.1.1 source 172.16.4.1 repeat 3
[피어 상태 확인]
show crypto isakmp peers
[SA 상태 확인]
show crypto isakmp sa
[연결 상태 확인]
show crypto engine connections active [연결 재시작]
clear crypto session remote 192.168.12.1
4) ESP - Main 모드
=================== <R1> ===================
# config 모드 진입
crypto isakmp policy 10
encryption des
group 2
hash md5
authentication pre-share
lifetime 60
exit
crypto isakmp key 1234 address 192.168.34.2
ip access-list extended R1R4
permit ip 172.16.1.0 0.0.0.255 172.16.4.0 0.0.0.255
exit
crypto ipsec transform-set KITRI esp-md5-hmac esp-aes
exit
crypto map VPN 10 ipsec-isakmp
match address R1R4
set peer 192.168.34.2
set transform-set KITRI
exit
interface serial 1/1
crypto map VPN
end
=================== <R4> ===================
# config 모드 진입
crypto isakmp policy 10
encryption des
group 2
hash md5
authentication pre-share
lifetime 60
exit
crypto isakmp key 1234 address 192.168.12.1
ip access-list extended R4R1
permit ip 172.16.4.0 0.0.0.255 172.16.1.0 0.0.0.255
exit
crypto ipsec transform-set KITRI esp-md5-hmac esp-aes
exit
crypto map VPN 10 ipsec-isakmp
match address R4R1
set peer 192.168.12.1
set transform-set KITRI
exit
interface serial 1/2
crypto map VPN
end
=================== <추가 확인> ===================
[동작 확인]
ping 172.16.1.1 source 172.16.4.1 repeat 3
[피어 상태 확인]
show crypto isakmp peers
[SA 상태 확인]
show crypto isakmp sa
[연결 상태 확인]
show crypto engine connections active [연결 재시작]
clear crypto session remote 192.168.12.1

============================================================
[ ESP 터널모드 - 부가 설명 ]
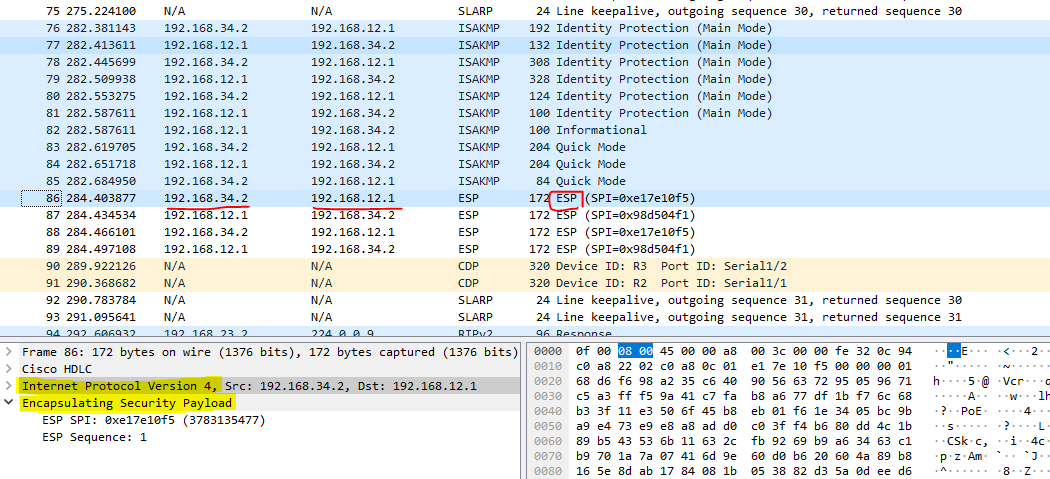
- 패킷 덤프 뜬 내용 보면 터널모드로 진입(Main Mode) 하면서 라우팅 처리된 New Header IP 로 보여짐
- Internet Protocol Version 4 (IPv4) : New IP Header
- New Header (라우팅 되도록 부여된 헤더 (라우터 기기 IP) - sniffing 되어도 괜찮음) : 192.168.12.1 / 192.168.34.2
- Encapsulating Security Payload : Original IP Header 값을 담고있음 (값 자체는 암호화 + 캡슐화되어서 볼 수 없음)
- ESP (패킷 전송 부분) 클릭하면 "Encapsulating Security Payload" 밑으로 Sequence 번호, SPI 번호만 알 수 있고, Original Header IP 값은 암호화 + 캡슐화 되어서 ESP 안으로 더이상 진입 불가
- Original Header (실제 헤더 - 숨김처리) : 172.16.1.1 / 172.16.4.1

'Unix Linux' 카테고리의 다른 글
| GRE 터널모드 (0) | 2024.09.03 |
|---|---|
| alias 등록 (0) | 2024.08.27 |
| Unix/Linux SSL 설정 방법 (Debian) (0) | 2024.08.20 |











